Sponsored by BioCatch
Sponsored by Lastline
Testing the Top 9 Market Leaders in Breach Detection: How They Measure Up
Sponsored by Lastline
Cybercrime Projected to Exceed $2 Billion by 2019: What You Need to Know
Sponsored by Symantec
How To Get The Best Balance Of Threat Prevention And Detection
Sponsored by BitSight
The Evolution of Vendor Risk Management in Financial Institutions
Sponsored by Fidelis Cybersecurity
What's Required in Your Next Generation IPS Solution?
Sponsored by VMware
24/7 Government - a Public Sector CIO Special Report
Sponsored by Hitachi ID
Best Practices for ID and Access Management (IAM) Implementation and Operation
Sponsored by Level 3
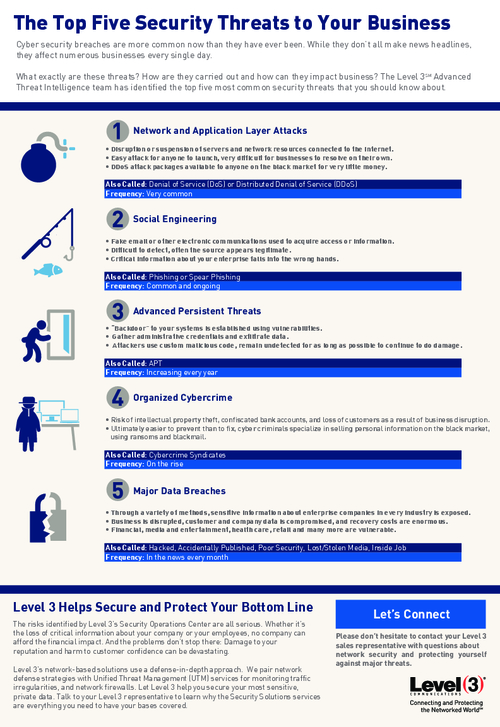
The Top Five Security Threats to Your Business
Sponsored by Terbium Labs
Demystifying the Dark Web: the Truth About What It Is, and Isn't
Sponsored by Level 3
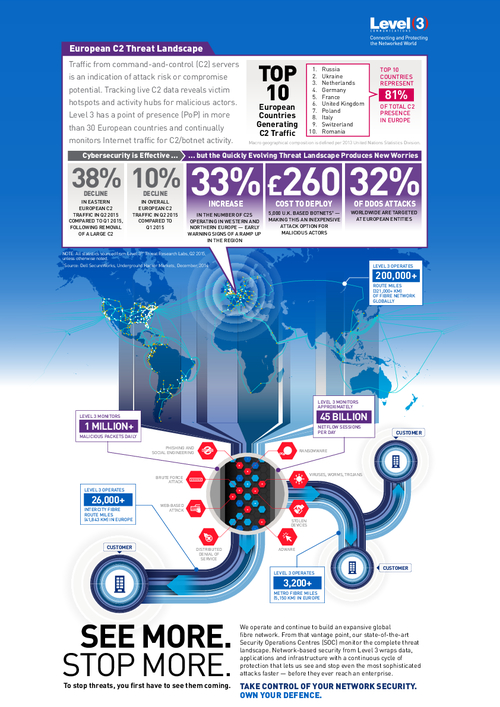
Quickly Evolving European C2 Threat Landscape Produces New Worries
Sponsored by Carbon Black