COVID-19 , Fraud Management & Cybercrime , Fraud Risk Management
US, UK Authorities Crack Down on Suspicious COVID-19 Domains
Scam Sites Used to Spread Malware, Steal Credentials, Officials Say
U.S. and U.K. law enforcement officials have shut down hundreds of suspicious domains with COVID-19 names and themes that have been used to support criminal efforts to steal credentials, spread malware and spoof government sites and programs.
On Wednesday, the U.S. Justice Department announced that it worked with a number of private companies to "disrupt" hundreds of online domains with COVID-19 names that prosecutors say are used for a wide array of scams.
See Also: OnDemand Webinar | Tackling Retail's Post-Pandemic Logistics Disruptions with Data-Driven Resiliency
Many of these domains and websites used names that incorporate the words "Covid19,” or Coronavirus," the Justice Department says.
Earlier this week, Britain's National Cyber Security Center announced that it had shut down over the past month more than 2,000 fraudulent websites used to carry out COVID-19 scams.
Domain Registrations
From mid-February to mid-March, there was a significant uptick in the number of domains registered that incorporate COVID-19 as a theme, according to research released this week by the COVID-19 Cyber Threat Coalition, a group of volunteer security researchers that is collecting pandemic-related threat intelligence (see: New Platform Collects COVID-19 Threat Intelligence).
The number of new domains registered that have a COVID-19 theme peaked at about 5,000 per day on March 20, but has since fallen to about 1,800 per day, according to the coalition report.
Over the last two weeks, security firm Check Point Software has tracked an average of 14,000 attacks each day that contain a COVID-19 theme. The vast majority of these incidents - approximately 94 percent - are phishing campaigns (see: UK and US Security Agencies Sound COVID-19 Threat Alert).
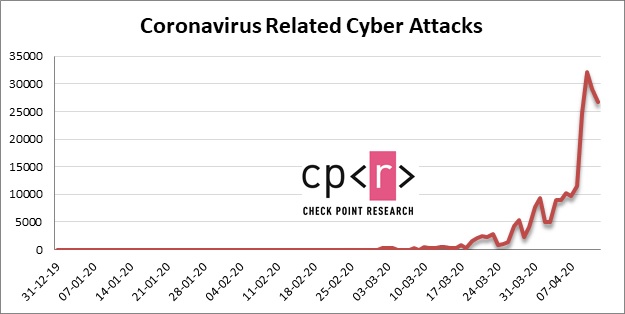
As of April 21, the FBI's Internet Crime Complaint Center had received more 3,600 complaints so far this year about fraudulent sites, many of which use domain names related to the COVID-19 pandemic, the Justice Department notes.
A Variety of Scams
The Justice Department reports that the suspicious domains haven been used for an array of scams, including:
- Spoofing the websites of legitimate companies and services in order to spread malware;
- Tricking victims into giving up their personally identifiable information, including banking details, by inputting this data into sites that spoof government programs and agencies;
- Stealing money by falsely claiming to collect donations to the American Red Cross for COVID-19 relief efforts.
In a separate move, the Justice Department has announced a task force designed to counter financial scams related to the $300 billion in stimulus payments being sent to U.S. citizens. In recent weeks, the FBI uncovered several domains that appeared to be designed to take advantage of the stimulus program (see: Economic Stimulus Payments: A Fraud Target).
UK's Crackdown
As part of its crackdown on more than 2,000 suspicious domains, Britain's National Cyber Security Center noted that authorities closed down nearly 470 online shops selling fake coronavirus-related items as well as another 555 sites were found to be distributing malware.
Another 200 suspicious domains shut down were created for phishing campaigns, while over 800 were designed to conduct advance-fee frauds, according to NCSC.
NCSC is urging U.K. citizens to report email scams that use COVID-19 themes or claim to offer services related to the coronavirus. Over two days this week, the Suspicious Email Reporting Service program flagged more than 5,000 suspicious emails, which resulted in more than 80 malicious domains being shut down, according to NCSC.