Cybercrime , Fraud Management & Cybercrime , Fraud Risk Management
Microsoft Exchange: Server Attack Attempts Skyrocket
Check Point Research Tracks Tenfold Increase in 5 Days
From Thursday through Monday, Check Point Research tracked a tenfold increase in the number of attempts to exploit vulnerable on-premises Microsoft Exchange servers as many organizations are still racing to install patches.
See Also: OnDemand | Identifying and Reducing Risk Faster in Multi-Cloud Environments
Global exploits of four vulnerabilities in Exchange servers grew from an estimated 700 on Thursday to about 7,200 on Monday as hackers continued to scramble to take advantage of the flaws before companies patched their systems, Check Point reports, citing results of its telemetry efforts.
"Cybercriminals and other malicious actors know there is a finite time to act between the announcement of a vulnerability and the point where patches are released and in place," says Saryu Nayyar, CEO of the security firm Gurucul. "That time is rapidly closing for the Microsoft Exchange vulnerabilities."
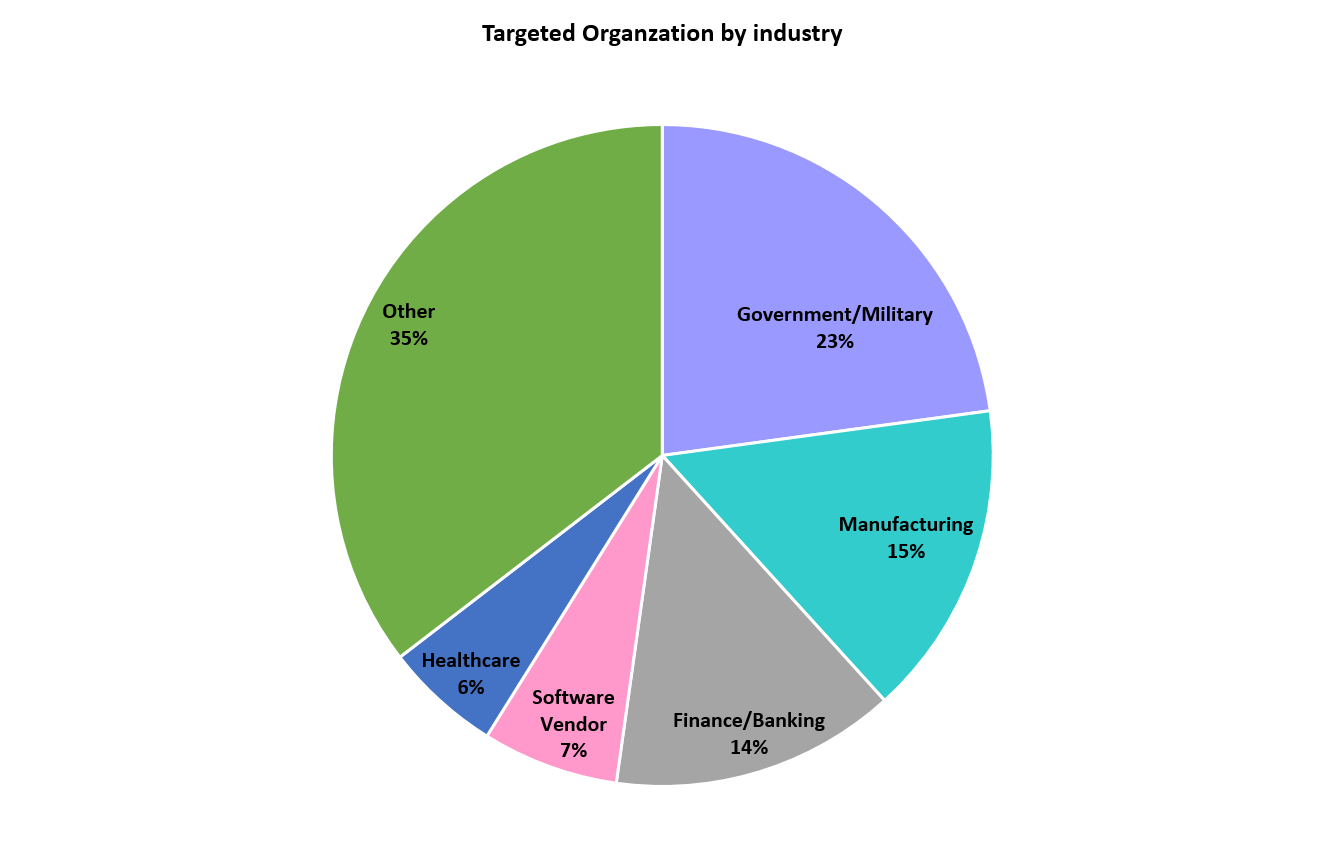
Check Point found that during the five-day period, 17% of the Exchange exploits targeted organizations in the United States, with 6% targeting Germany, 5% each for the U.K. and the Netherlands and 4% in Russia. Some 23% of all attacks were aimed at the government/military sector, followed by manufacturing, finance/banking, software vendors and healthcare.
Patching Challenges
Although the technical aspect of patching is not necessarily difficult, installing the update can cause issues with email availability, says Lotem Finkelsteen, Check Point's manager of threat intelligence.
"Usually, organizations have more than a single Exchange server," he says. "Therefore, it requires organizations to shut down these exchange servers, which they have to plan very carefully."
Aaron Fosdick, CISO at the penetration testing firm Randori, offers a similar perspective: "If you have 1,000 users, you feel the pressure to have an upgrade that doesn't impact availability at all."
To help smaller organizations that cannot immediately implement a patch, Microsoft has released an interim mitigation tool that allows them to take quick action to prevent attacks that exploit the unpatched ProxyLogon flaw in on-premises Microsoft Exchange servers.
The security firm RiskIQ estimated today that more than 400,000 on-premises Exchange servers remained unpatched - the majority located in the U.S.
Tracking Source of Exploits
Microsoft initially reported that a China-based group it calls Hafnium had exploited the four vulnerabilities - CVE-2021-26855, CVE-2021-26857, CVE-2021-26858, and CVE-2021-27065.
But security researchers at ESET say that at least 10 advanced persistent threat groups have been exploiting vulnerable on-premises Exchange severs at thousands of companies since early January (see: Microsoft Exchange: At Least 10 APT Groups Exploiting Flaws).
Some Exchange servers with the unpatched ProxyLogon flaw are being targeted by DearCry ransomware, which security company Sophos describes as "unsophisticated" and apparently "created by a beginner."